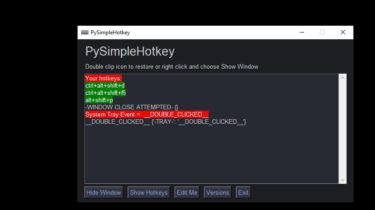
A hotkey manager that runs in the system tray
PySimpleHotkey A hotkey manager that runs in the system tray. Uses PySimpleGUI for the GUI and the system tray. This project uses these pip installable packages: PySimpleGUI psgtray keyboard This project is a mash-up of some PySimpleGUI demo programs and a program called pingmote. The pingmote project is the origin of the keyboard handler. A big thank you to @dchen327 for the code and inspiration. The system tray code is from the psgtray demo program. The 2 utilities that are […]
Read more