Flickr Downloader – A tiny Python tool can download all public photos of a user, even though they’re disabled
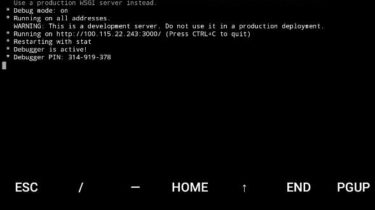
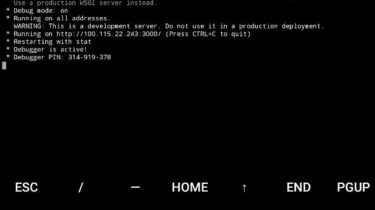
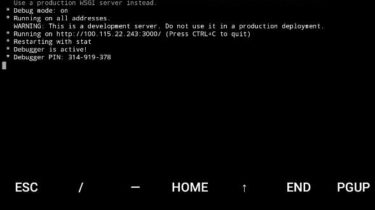
This tiny Python tool can download all public photos of a user, even though they’re disabled. Prerequisite We need Python Requests to scrape, BeautifulSoup to download and FlickrAPI to get photo IDs. pip install requests pip install html5lib pip install bs4 pip install flickrapi Usage There is only one feature, just run then enter the user ID: You can get the user ID from profile URLs, example 12345678N00 from: https://www.flickr.com/people/12345678N00/… https://www.flickr.com/photos/12345678N00/… This tool will try to download the largest size […]
Read more