Detector for Log4Shell exploitation attempts
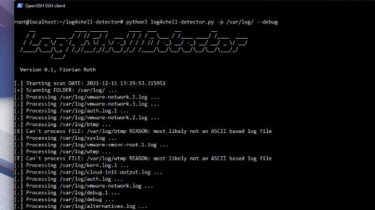
Detector for Log4Shell exploitation attempts
Idea
The problem with the log4j CVE-2021-44228 exploitation is that the string can be heavily obfuscated in many different ways. It is impossible to cover all possible forms with a reasonable regular expression.
The idea behind this detector is that the respective characters have to appear in a log line in a certain order to match.
Split up into a list it would look like this:
['$', '{', 'j', 'n', 'd', 'i', ':', 'l', 'd', 'a', 'p', ':']
I call these lists ‘detection pads’ in my script and process each log line character by character. I