Operational information regarding the Spring4Shell vulnerability in the Spring Core Framework
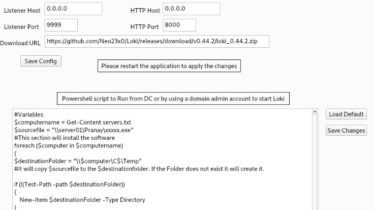
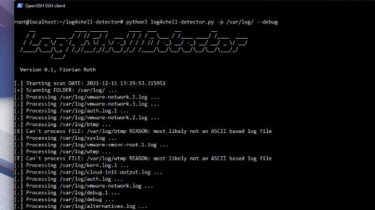
Operational information regarding the Spring4Shell vulnerability (CVE-2022-22965) in the Spring Core Framework. Repository contents README.md: contains general information and detection and mitigation measures software/README.md: contains a list of known vulnerable and not vulnerable software. services/README.md: contains a list of known vulnerable and not vulnerable services. NCSC-NL has published a HIGH/HIGH advisory for the Spring4shell vulnerability. Normally we would update a HIGH/HIGH advisory for vulnerable software packages, however due to the expected number of updates we have created a list of […]
Read more