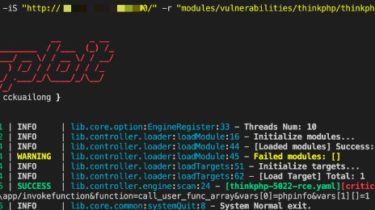
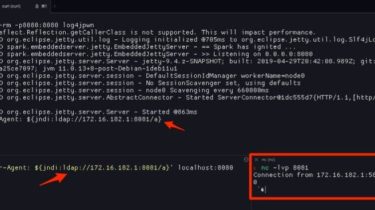
A lightweight, flexible and novel open source poc verification framework
中文 README pocsploit is a lightweight, flexible and novel open source poc verification framework Pain points of the POC framework in the market There are too many params, I don’t know how to get started, but only some of them are commonly used. YAML poc framework(like nuclei & xray) is not flexible enough. the conversion cost is very high when writing poc. Sometimes it’s hard when encountering non-http protocols. (only hex can be used) Sometimes POC has false positives, which […]
Read more