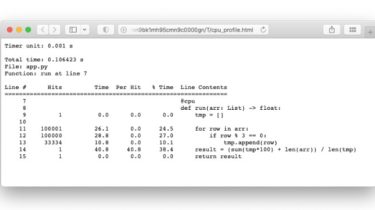
CVE-2022-22965 poc including reverse-shell support
CVE-2022-22965 poc including reverse-shell and password support. Feel free to add more stuff 🙂 $ docker run -p 9090:8080 vulfocus/spring-core-rce-2022-03-29 # run vulnerable docker $ python3 exploit.py -c id –password 1234 –shell_name big0us $ python3 exploit.py –help # for more usages I refactored the code of the original exploit and add some features reverse shell suport password support shell name support GitHub View Github
Read more